
Your help desk is your weakest link.
The MGM breach started with a 10-minute phone call. We test if yours would fall for the same attack.
The help desk is a privileged bypass
External help desks sit on the shortest path to "reset the password, unlock the account, grant the access." They're also uniquely exposed:
01. BLAST RADIUS
IAM-level power, broad access, minimal oversight. One compromised agent = massive blast radius.
02. ACCESS SPRAWL
High turnover, stale credentials, contractors with lingering access. A supply chain nightmare.
03. LOW-TO-NO VISIBILITY
No access to your SIEM, your EDR, your playbooks. You're flying blind.
Test the workflows attackers actually use against help desks
GhostEye safely tests your external support team for social engineering risk. We find the gaps in verification, escalation, and access controls.

We plant controlled canaries in your environment. Can an attacker turn your help desk into a credential pipeline?
We build fake identities that look like your real employees. Role, location, manager — everything checks out.

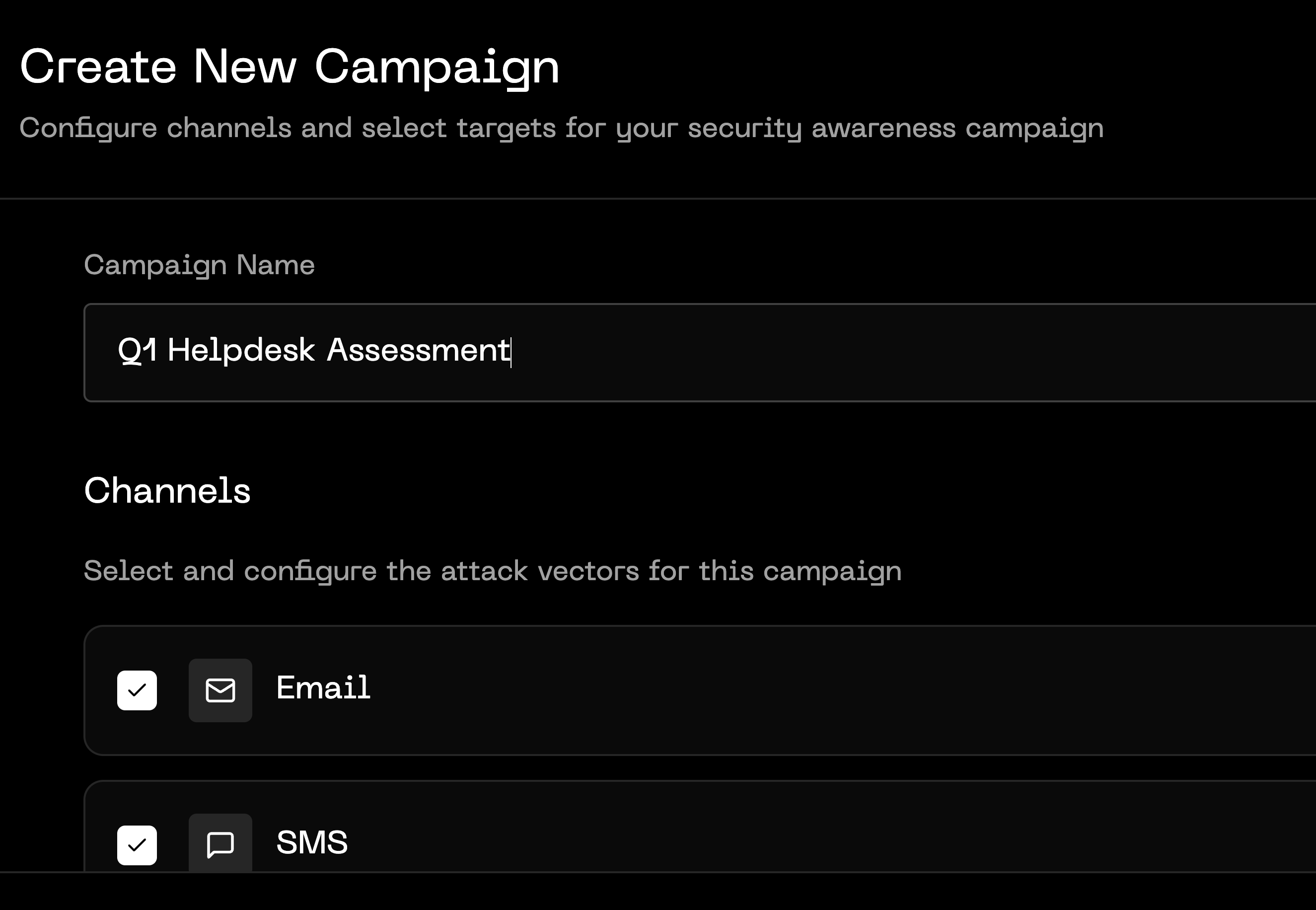
We run the full attack: first contact → social engineering → privileged access. Just like the real thing.


When they fail, training fires immediately — tailored to exactly what went wrong.
See how your help desk holds up against a real social engineering attack.
One phone call took down MGM. We simulate the same attack: AI voice agents using real OSINT to social engineer your help desk. Get a full report on what worked, what didn't, and how to fix it.

